TL;DR
Tailscale is great and as easy or easier than they make it sound. You should do it. Mostly this walkthrough is so you can see how easy it actually is and then be motivated to do it yourself.
Intro (what are we talking about?)
Wireguard® is a new(ish) replacement for OpenVPN (and IPsec). It’s much more modern, and focused on being simple and cryptographically sound. There are anecdotal reports of speed increases over OpenVPN protocol usage in the realm of 40 - 50 percent. It’s just super great in really all the ways. But it can be tricky to set up…
Tailscale is a very new company, and they’ve built a few layers of abstraction on top of Wireguard while also sprinkling in some neat extra stuff, like 2FA you’re probably already using to replace access control concerns. Basically, they’ll give you a static IP address that’s tied to your 2FA identity (the free plan uses gmail and gives you 100 devices), and then any machines you authenticate with that account can now see every other of your devices and trust their VPN IP even as the real-world IP changes and moves around. Not part of the VPN? Then the IP just doesn’t resolve. (You can read much more about the internals of what they’re doing if you want to dig in.)
It honestly feels like magic when you do it, which is why I’m posting all of this so you can see how little it actually takes to get there.
Setup
-
Sign up for an account.
-
You’ll do the familiar OAuth dance of logging into or selecting your gmail account, then be automatically redirected to an account page (of sorts).
Nothing to see there… -
Install Tailscale on computer A. They have simple instructions for lots of Linuxes, and Windows, OSX, and iOS (Android is coming soon). [I hit my 10 link posting limit, so individual links to the install instructions got axed–sorry.]
I used Linux, so I added a repo, installed a single package, and then ran a single command:
sudo tailscale up. That returned a URL to paste into a browser to verify I could authenticate with the same account I set up with above, but since it’s gmail and I was logged in already, I didn’t actually have to click on anything and got redirected to a page that said my device was added and I could close the tab now. (Not as helpful as a “next steps” link, but certainly no complaints about ease).OSX has an app in the App Store that looks like it does everything nicely in the same window.
-
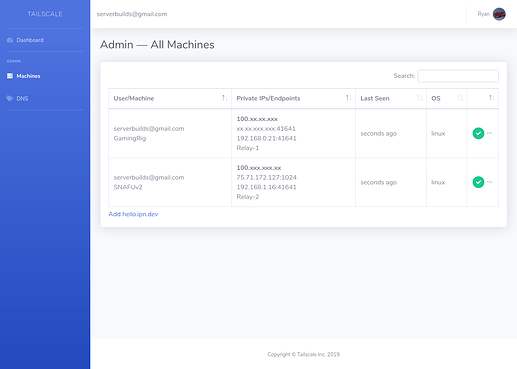
Now you have an IP in their protected 100.xx.xx.xx range for that machine. Any additional computers you install the app onto and then authenticate with the same email account…just…see each other.
I changed the IPs (and computer names) in that screenshot, but we’re all done here… That’s really it.
I typed in the IP of my home machine from my laptop while I was out and it immediately brought up my Apache root directory from my local setup at home. I modified /etc/exports to bind a directory to my laptop’s 100.xx Tailscale IP and now I can NFS mount it from anywhere and there all the files are. Any services running on any other machine are just available. To any other machine. It’s the goddamn future!
Considerations
- The URL to that management panel isn’t linked very well from any of their other pages. It’s here: Tailscale
- You have to know the IP addresses… There are some DNSy things you can sort of do on their platform, but actually mapping something you can remember to the IPs isn’t a feature that exists (yet?!).
- They force periodic key rotation for security, but you can disable it per-node in that admin panel if you’re running it on an embedded device where jumping back through the 2FA auth isn’t practical.
- ??? I don’t know. I’m still pretty high from how well this works.
They’re open sourcing much of the platform if you want to follow along, or if you’re into Go and want to pitch in: GitHub - tailscale/tailscale: The easiest, most secure way to use WireGuard and 2FA.
I can’t wait to see what else happens here. I hope some of you give this a shot and are as into the taste of their koolaid as I am.