This guide was written for pfSense 2.4.x with pfblockerNG 2.1.x. As of pfblockerNG v3.1.0 and later, included with pfSense v2.5.2 and later, this guide is now obsolete. pfblockerNG 3.x.x and up is a complete overhaul both visually and under the hood. The steps in the guide are no longer valid and cannot be followed. It is provided from here on as an archival copy only.
This guide was written for pfSense 2.4.x with pfblockerNG 2.1.x. As of pfblockerNG v3.1.0 and later, included with pfSense v2.5.2 and later, this guide is now obsolete. pfblockerNG 3.x.x and up is a complete overhaul both visually and under the hood. The steps in the guide are no longer valid and cannot be followed. It is provided from here on as an archival copy only.
Introduction
This guide will get you started with blocking ads on your pfsense router using a package (plugin) called pfblockerNG. This package is functionally similar to the popular standalone tool ‘pihole,’ with the added bonus of integrating directly with your pfsense router. It’s a much more robust solution than just using adblocking extensions in your browser (though we will cover that, along with added benefits of combining the two, later on).
With pfblockerNG you can ensure that ads will be blocked across your entire home network. You can use prebuilt ‘EasyLists’ and also subscribe to popular user maintained blocklists. We will cover setting up both. pfblockerNG is also smart enough to handle the overlap from duplicate entries in the routing table, so don’t worry if your selected lists might have matching entries.
0. Prerequisites
Before we get started, we will need to edit the firewall to handle the increased amount of Firewall Table Entries for these lists. Without increasing this value, DNS queries take much longer, causing webpages to load very slowly.
- Navigate to System / Advanced / Firewall & NAT and locate Firewall Maximum Table Entries. The default value for this setting is 400000. You can safely set it to 2000000 for the purpose of this guide.
Realistically you can set it much higher, but be weary of setting this too high as it directly uses more RAM the higher you set it. Tested on 4GB of RAM, my own fairly basic install sits idle at ~25% RAM in use. YMMV depending on your config and workload.
Note:
pfblockerNG only functions with the DNS Resolver service active. It will not function with the DNS Forwarder service active. If you need DNS Forwarding functionality, I highly recommend enabling forwarding mode in the DNS Resolver service. Click here for more info.
1. Install pfblockerNG
- Navigate to System / Package Manager / Available Packages and locate pfblockerNG. Click The Install button and wait for it to complete.
2. Enable pfblockerNG
By default, all packages are disabled after installation.
- Navigate to Firewall / pfBlockerNG / General and check the box for Enable pfBlockerNG.
- Scroll to the bottom of the page and click the Save button.
3 - Set The Cron Update Schedule
- On the same tab, locate CRON Settings. Set the desired frequency interval to update your block list(s).
I find once a day is ideal. - Scroll to the bottom of the page and click the Save button.
4. Enable DNSBL
- Navigate to Firewall / pfBlockerNG / DNSBL and check the box for Enable DNSBL. Scroll to the bottom of the page and click the Save button.
2. Optional: TLD (click me)
TLD: Top-Level Domain
If you have a lot of RAM (see memory usage details below), you may wish try out a beta feature called TLD. This setting enables additional processing to block ALL sub-domains for advanced blocking. For example, a list with forums.serverbuilds.net would also result in serverbuilds.net and all of it’s subdomains being blocked with TLD enabled. Please note that TLD is a beta feature of pfsense.
- Locate DNSBL Firewall Rule - If you only have one LAN interface, leave this setting unchecked and proceed to Step 5.
If you have multiple LAN interfaces, select each interface to protect and then check the box.- Scroll to the bottom of the page and click the Save button.
TLD greatly increases memory usage!
Using more and/or heavier custom block lists will increase the amount of RAM needed for DNS resolution to function properly. Without enough RAM for TLD, you may experience errors and slow or failed webpage loading.
Reference total domains to determine how much RAM to allocate for TLD. Please note that the table below is a guideline for RAM amount needed ONLY for the TLD processing, NOT total amount of system RAM.
TLD Domain Limit Restrictions:
RAM Domains < 1.0GB RAM Max 100k Domains < 1.5GB RAM Max 150k Domains < 2.0GB RAM Max 200k Domains < 2.5GB RAM Max 250k Domains < 3.0GB RAM Max 400k Domains < 4.0GB RAM Max 600k Domains < 5.0GB RAM Max 1.0M Domains < 6.0GB RAM Max 1.5M Domains < 7.0GB RAM Max 2.5M Domains > 7.0GB RAM > 2.5M Domains
5. Setup EasyLists
- Navigate to Firewall / pfBlockerNG / DNSBL and click the DNSBL EasyList tab. Set DNS Group Name, and Description to anything you’d like, for example “Easylist.”
- Set EasyList Feeds to:
- State: ON
- EasyList Feed: EasyList w/o Elements
- Header/Label: Easylist
- Highlight each category by selecting each one (CTRL + Click to select multiple).
- Set List Action to Unbound.
- Set Update Frequency to be at least as often as your cron update schedule in Step 3.
I find once a day is ideal. - Scroll to the bottom of the page and click the Save button.
6. Setup Custom Lists
For this step, I had previously provided only a single, popular, user maintained list found on reddit, which has now moved to it’s own hosted domain. You can find site and info here and the list here. This list is what I found to work best for me, but because no blocklist is perfect, I encourage you to do research and find what works best for you. There is no one size fits all.
Here is a well maintained source of lists. Please read the page and descriptions to understand what might work best for your needs. Alternatively, feel free to research and add your own favorite block lists from other sources for this step.
- Navigate to Firewall / pfBlockerNG / DNSBL and click the DNSBL Feeds tab.
- Click the +Add button.
- Set DNS GROUP Name and Description to anything you’d like, for example “Custom.”
- Set DNSBL to:
- Format: Auto
- State: ON
- Source: [Your block list URL]
- Header/Label: Custom Name
- Set List Action to Unbound
- Set Update Frequency to be at least as often as your cron update schedule in Step 3.
I find once a day is ideal. - Scroll to the bottom of the page and click the Save button.
Repeat Steps 6.1 through 6.7 for each additional list you add. Please keep in mind adding more lists may impact performance and can vary with each list.
7. Update Lists
Updates are run on the schedule set in Step 3. However, the first one must be initiated manually to take effect immediately.
- Navigate to Firewall / pfBlockerNG / Update. Click the radio button for “Update” and click the Run button.
- Observe the log viewer as the update processes and allow it a couple minutes to finish.
And that’s it! …almost
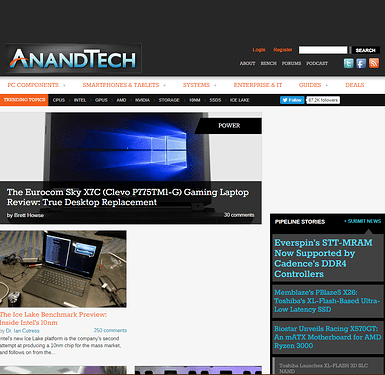
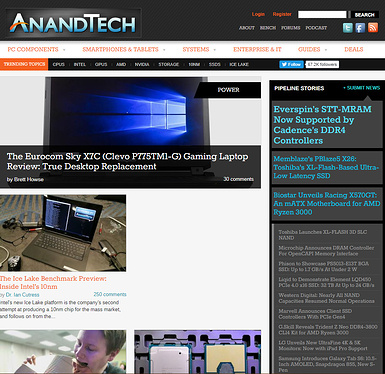
After the initial update, you should notice ads are now being blocked in your browser. Anandtech.com is a well laid out site to test. You should be well on your way to adblocked nirvana…
But wait, it’s still ugly!
You’ve probably noticed by now, ads that are blocked leave behind the spaces set aside for them. This looks especially bad on some sites, or is just distracting. Here’s where combining adblock efforts with a browser extension are still particularly useful.
Some Adblock Extensions, like uBlock Origin, have a built in feature called Cosmetic Filtering. This is for rearranging websites with blocked ads to look more natural, as if the ad never existed. It really helps clean up the spaces left behind on most sites.
The added benefit here is that pfsense is now tackling the adblock workload, leaving your browser extension free to process cosmetic filtering much faster. Most, if not all ads will never even reach your browser. Here are comparison shots:
tl;dr - Simply install uBlock Origin to make websites pretty again. Have your cake and eat it too.